Mapping 11,326 products to NIST CSF 2.0
At IT-Harvest we set out to harvest all the data on the cybersecurity industry and put it in a searchable database. There are certain questions that cannot be answered without starting with a data collection effort. Like: how many cybersecurity vendors have added headcount in 2025? (Answer: 1,912 out of 3,956, or 48%). We launched the IT-Harvest Dashboard on March 30, 2022 with just such questions in mind.
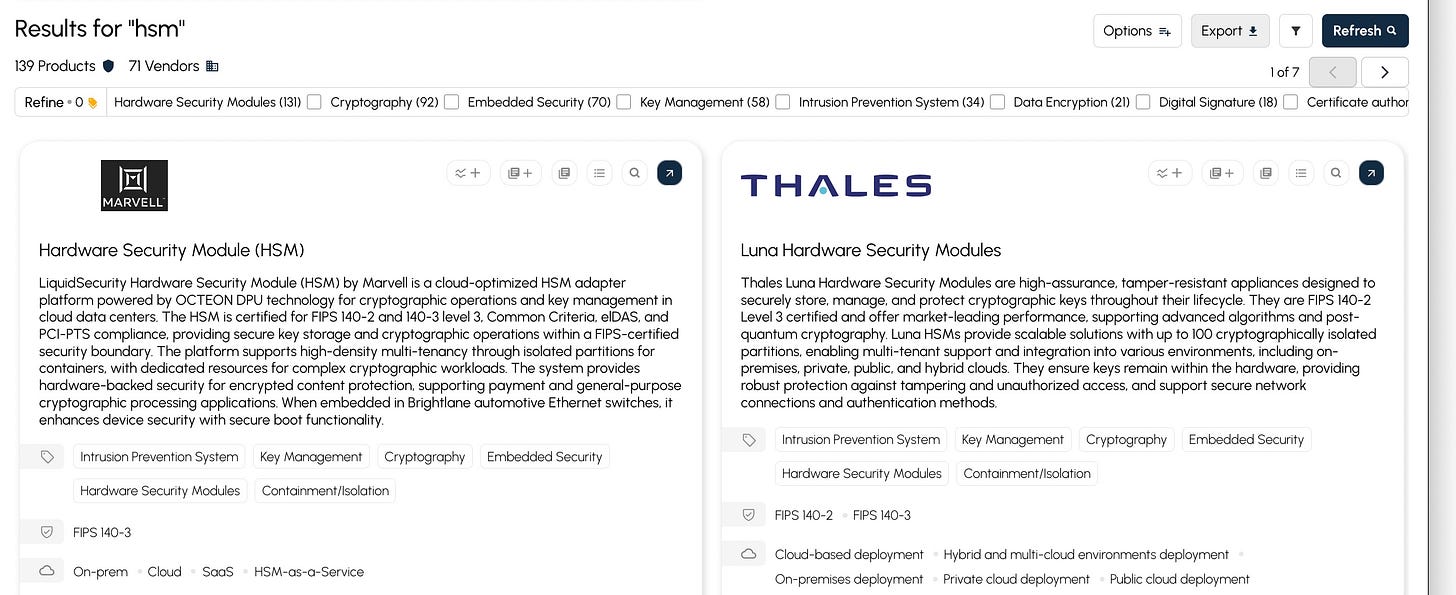
Once you have collected a list of all the vendors in cybersecurity, a new realm of possibilities opens up. Using automation and AI you can ingest and normalize product descriptions. A database of 11,326 cybersecurity products allows you to answer questions like: find all the hardware security module (HSM) solutions. There are 139!
Once you have all the products in a database you can do additional processing, like mapping to compliance frameworks. We launched the product database in late 2023 with mappings to MITRE ATT&CK and have since layered in MITRE Mitigations.
Every CISO we showed this to asked for NIST Cybersecurity Fraemwork mappings. We announced that on July 12 of 2024 (Yes! We have NIST!) If, during an audit or survey of your NIST coverage you discovered a subcategory that you lacked controls for you can now immediately search based on Category or Subcategory!
There are also new questions that you can ask. Which NIST CSF Category has the most solutions? Which has the fewest? Well…
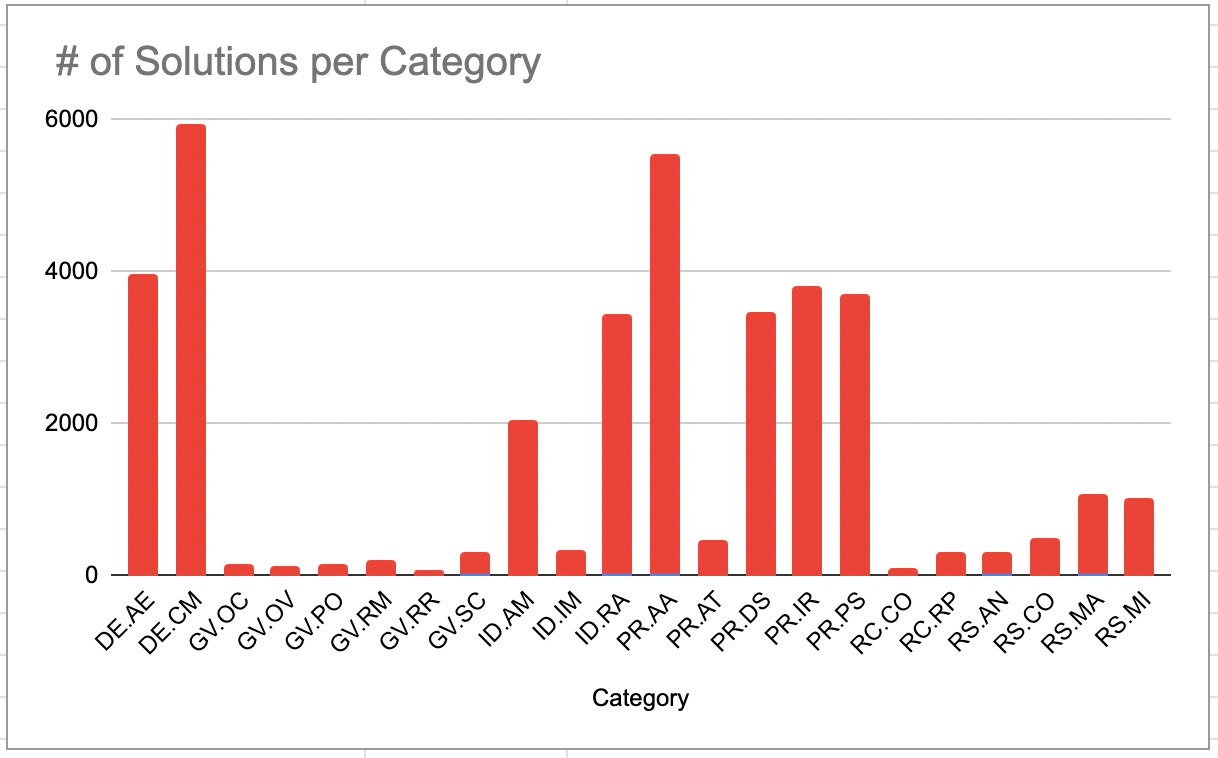
For the first time ever. Here are the number of solutions per NIST CSF Category.
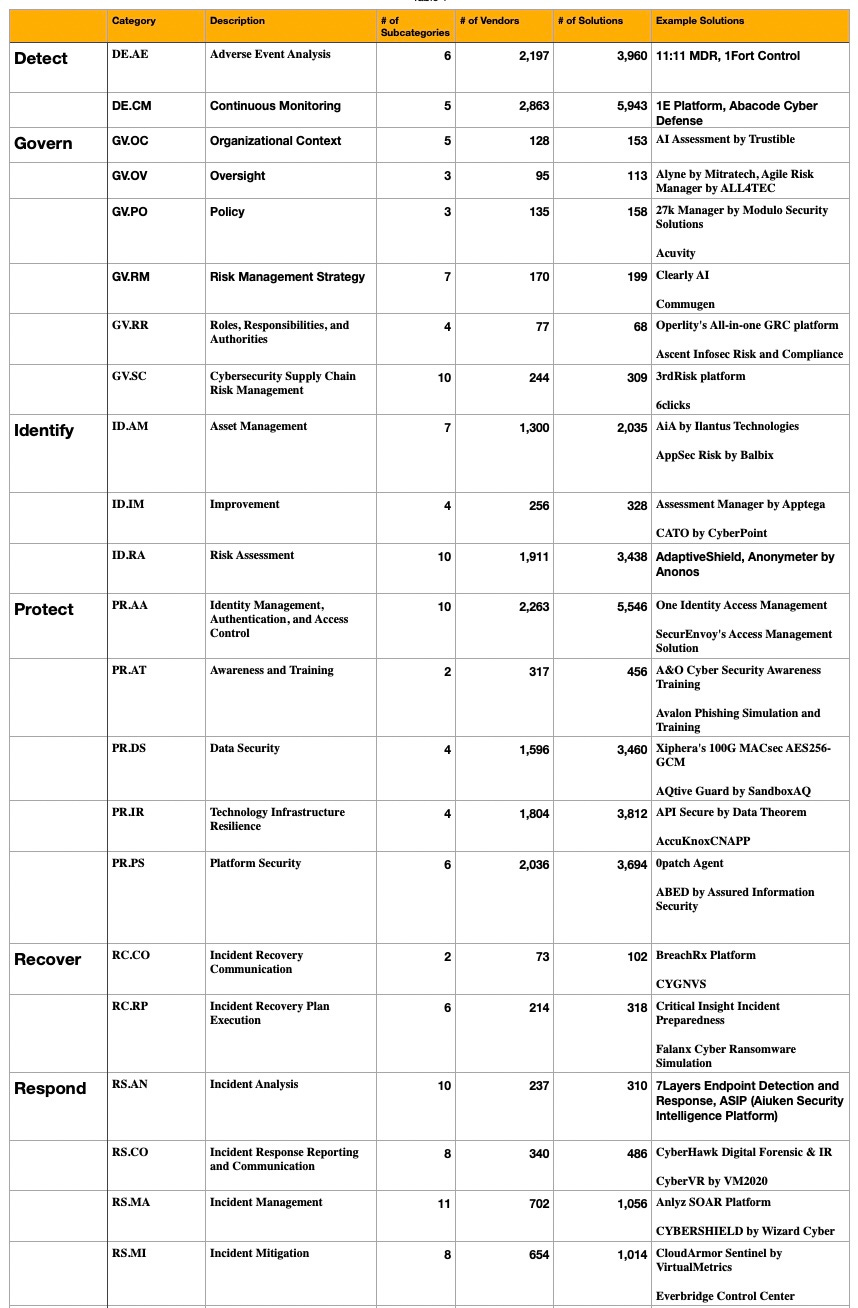
And in table form:
Some observations. The creators of the Cyber Security Framework did not have visibility into the entire solution space. Perhaps a product focused lens would have created a different hierarchy.
No surprise that Continuous Monitoring has so many solutions (5,943). It is a feature of many other products from other Categories.
One big surprise is that the Governance Category is so thinly covered. A surprise because GRC is the biggest category for vendors with 601 out of 3,956 tracked in the Dashboard.
There is no way that having products in your security stack that map to all the Categories means you have full coverage. You would need to have products that map to all of the subcategories. To see that, reach out for a demo.
If you sum the column for # of Solutions you get 36,958 which indicates that the average product covers 3-4 subcategories. In other words, you don’t need a stand alone product to map to each of the 135 Subcategories. Maybe 33-45 tools should be the goal for adequate NIST coverage?
Of course there are many tools that will not map to any NIST subcategories, but are still essential to operations.
Next up we are going to introduce a capability that will be welcomed by many security teams. The problem to be addressed is product rationalization. I have talked to a UK bank that has 750 tools. Most estimates put the average enterprise having 60-75 cybersecurity tools. I think the number is greater than that. There is growing demand to rationalize or at least optimize tool sets. Consultants are being paid hundreds of thousands to engage in projects that identify, map, and expose gaps and overlaps.
One approach would be to map an entire security stack to NIST CSF 2.0. If certain subcategories seemed to be overly covered that may guide an organization’s efforts to eliminate redundant tools. Or, there may be significant gaps in coverage indicating the need for more tools.
If you had all the mappings in one place couldn’t you build a tool to instantly complete this task? If you did, what would it look like? We have some ideas. Stand by…
Update. October 20. See the announcement and demo of Security Stack Analysis.