I love this column titled The Yellow Page Problem of Private Markets. The author, Leopold Gasteen, CEO and Co-Founder of DeckMatch, contributed this column to the Data Driven VC. His primary point is that just tracking company data does not solve the primary problem which is finding competitors.
“This is the Yellow Pages Problem of private markets: we've built increasingly sophisticated databases that tell us everything about a company except what it actually does. We know their headcount fluctuations, funding history, and the schools their founders attended. We can track their job postings, their office locations, and their tech stack.”
At IT-Harvest we traveled the same road of discovery. Like Leopold we found that Pitchbook, Trackxn, and Crunchbase were horrible for actual discovery of competitors. Our edge, that led our users to say “100 times better than Pitchbook!” was that I categorized every single one of the 4,188 cybersecurity vendors (and still do). That process was simply a matter of visiting each website and putting them into one of 18 major buckets. Then I would just jot down what they do as a sub category. We have 660 of those. If you have ever experienced the frustration of trying to figure out what a vendor does from their website you will understand how it took me over 4,000 hours over five years to do so. Part of that time was evaluating and discarding thousands of companies that Pitchbook classifies as cybersecurity but are resellers, distributors, and consultants.
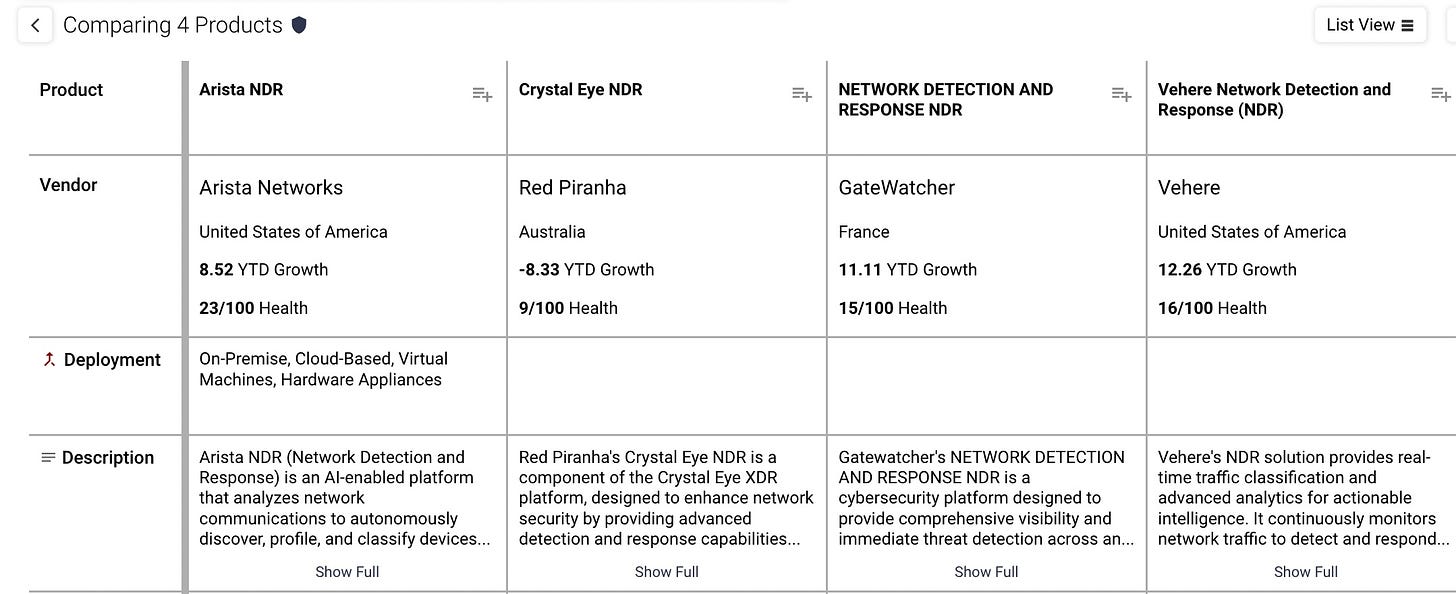
Leopold’s big insight is that you need to look at products to truly identify competitors. It is a little over a year since we had the same aha! moment. Look at Palo Alto Networks for instance. By any measure they are in the Network Security category and the UTM/NGFW subcategory. But PAN has many products that compete directly with many startups. If your platform can not identify that PAN is a direct competitor to Wiz you have a problem. Collecting data on all products is the solution.
Thankfully, vendors may completely hide what they do on their websites, but they cannot hide what their products do. Product descriptions *must* be written to capture SEO so prospects can find them. An NDR vendor *must* use key words like netflow, sflow, and full packet capture, to describe their product. A Digital Risk Protection company *must* use words like threat intel, feed, OSINT, and dark web.
So last year we began to systematically ingest all vendor product data from each vendor. We search for integrations, use cases, compliance regimes, and deployment data. We enrich the product data by doing the heavy lifting required to align each one with NIST CSF 2.0 controls and MITRE Enterprise and Mitigation models.
With complete product data you can find competitors by product, not just category.
But market research is only a small part of the value of having all product data in one place. You can use that to data to find products that meet your needs. You can search by keyword, usage, and integrations. Do you need a cloud based SIEM that integrates with Jura? Here’s a list! Do you need a hardware security module? Here are 37 from 22 vendors.
Stand by as we continue to expose value from universal cybersecurity product knowledge. If you have a need to understand your own product stack and discover your gaps and overlaps, schedule a demo with us to discuss.
You can play around with our data on the Cyber 150 by signing up for free at dashboard.it-harvest.com
Additional Notes
YAHOO is an acronym for Yet Another Hierarchically Organized Oracle. It was a complete rip-off of Yanoff’s List which was the most popular directory of websites back then. Jerry Yang, I suspect, picked the name to evoke Yanoff’s List and appear next to it in any directory of directories. In the ‘90s I saw an astoundingly bad take on the newly IPO’d Yahoo! that claimed that the value in the company was its ingenius branding. I reached out to Scott Yanoff who was an IT admin in Milwaukee by then. I asked him how often he thought of the missed opportunity for Yanoff’s List. He replied, “Every day.”
The first concept for the Security Yearbook series was inspired by the Thomas Register. This was a collection of twenty or so big volumes of mechancial components for manufacturing and prototyping. When I graduated in 1982 there was at least one set of the Thomas Register in every design shop I visited.
I even have early mockups of my book titled the Security Register. I finally realized that close to zero people would get the connection. :-)
Like the Thomas Register which stopped publishing and went digital, we also transitioned to digital with the IT-Harvest Dashboard. On top of that we introduced products, so are very similar. The rebranded ThomasNet is still going strong. If you are interested in manufacturing definitely sign up for their news letter.