A Deep Dive Into Cybersecurity
A Detailed Table of Contents for Examining Modern Threats and Solutions
Two days ago I created several examples of Google’s new AI tool called NotebookLM and posted them here. If you, like I do, love that feeling of awe and wonder that comes from seeing/hearing things that are just unbelievably spectacular, you should go listen to the audio files I uploaded. Or go to the bottom of this post and hear a podcast generated by AI of two people riffing on the content of Stiennon on Security. This is a collection of my essays from a ten year period starting in 2010. I published this in the beginning of Covid when I found myself with time on my hands.
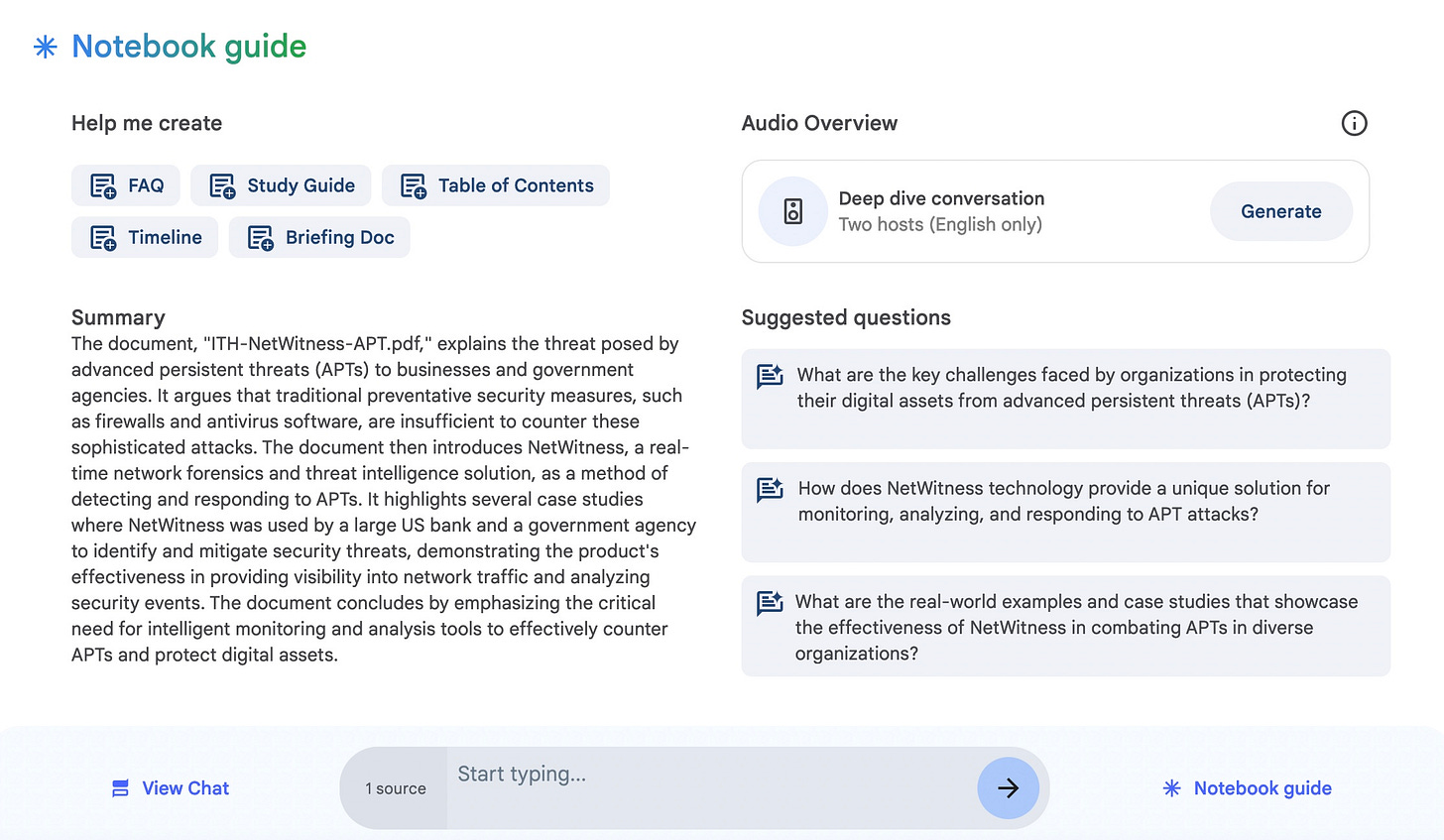
The podcast DeepDives are amazing. Now look at the other features of NoteBookLM. Here is what you see after you upload a document, in this case a whitepaper I wrote for Netwitness many years ago.
After I had uploaded Stiennon on Security and listened to the podcast (which is mind blowing, scroll to the bottom to listen to it), I clicked on Table of Contents, just one of the other functions. NotebookLM produced the following: a complete listing of every essay with a one sentence synopsys. To a writer or a student this is just as mind-blowing as the mind-blowing podcasts.
A Deep Dive Into Cybersecurity: A Detailed Table of Contents for Examining Modern Threats and Solutions
By Source (Richard Stiennon's IT Security Blog):
2010
March 18, 2010: Google's Moral Dilemma in China
This short post explores the balance between providing information access and navigating censorship, suggesting a decoupling strategy for Google in China.
April 9, 2010: Keep Austin Weird, but Use Good Password Controls
Using a car dealership incident as a backdrop, this post emphasizes the importance of robust password controls and network security practices for businesses, especially concerning disgruntled employees.
April 9, 2010: Is China Testing Cybernukes?
This post raises concerns about the potential for BGP route announcements to disrupt internet functionality, highlighting a critical vulnerability and speculating on China's capabilities.
June 16, 2010: Cyber Command Should Not Be Modeled on Strategic Command
This post criticizes the overreliance on military metaphors in cybersecurity, arguing for a nuanced approach to internet threats while analyzing Senator Levin's questioning of Keith Alexander's suitability for leading CYBERCOM.
June 16, 2010: Joint Intelligence Threat and Vulnerability Assessment
This post dissects a section of a government report mandating a cybersecurity assessment by various agencies, expressing skepticism about the effectiveness of the Einstein program and calling for more modern security approaches within the DHS.
June 16, 2010: The Ten-Year-Old Cyberwar Debate Continues
Revisiting a 2001 report by Ralf Bendrath, this post analyzes the evolution of the term "cyberwar," emphasizing the need for diverse operating systems beyond Windows for critical infrastructure and promoting open-source security research.
July 7, 2010: Bottom Line: Assume That You’ve Been Hacked
This post urges organizations to operate under the assumption of a security breach, highlighting the prevalence of data exfiltration and emphasizing the need for proactive security measures.
August 12, 2010: Why Intel Should Not Buy McAfee
This post analyzes the potential downsides of Intel's acquisition of McAfee, arguing that it dilutes Intel's brand and questions the strategic rationale behind the move.
September 3, 2010: The Good, the Bad, and the Ugly in the Pentagon's Cyberstrategy
This post dissects William Lynn’s cyberstrategy outlined in Foreign Affairs, praising the acknowledgement of cyber attacks but criticizing the reliance on outdated intrusion detection systems and advocating for more advanced security measures.
2011
April 28, 2011: Anatomy of a Targeted Attack
This post details a concerning trend of increasingly bold cyber attacks on strategic industries, highlighting incidents involving India’s military networks and large energy companies and calling for urgent security improvements.
May 3, 2011: How Reputation Services Enhance IPS
This post explores the integration of reputation services into Intrusion Prevention Systems (IPS) to enhance accuracy and performance, emphasizing the importance of reliable and scalable reputation databases.
May 9, 2011: The New Entrust: Is 2011 the Year of PKI?
This post discusses the changing landscape of the digital certificate business, referencing Entrust's surprising financial results and interviewing CEO Bill Conner on the growth of Public Key Infrastructure (PKI).
May 18, 2011: Demystifying Next-Gen Firewalls and UTM
This post examines the evolution of network security, providing a high-level overview of industry changes and analyzing the rise of Next-Generation Firewalls and Unified Threat Management (UTM) solutions.
June 14, 2011: Is Anyone Safe? Spate of Incidents Raises Security Concerns
This post highlights the vulnerability of even highly secure organizations, citing breaches at RSA, CitiBank, and others, and emphasizes the need for advanced security measures like those offered by Corero Network Security.
June 28, 2011: Interview with ActiveGuard CEO, Joel Lippert
This interview with Joel Lippert, CEO of ActiveGuard, delves into their security approach, focusing on their Security, Engineering, and Research Team (SERT), their multidisciplinary approach, cloud security services, and partnerships for integrated security solutions.
July 25, 2011: The Three Paths to Cloud Security
This post outlines three primary strategies for cloud security: Cloud-Washing, Cloud-Enabling, and Security as a Service. It discusses the strengths and weaknesses of each approach and highlights Trend Micro as a leader in securing cloud environments.
November 2, 2011: It's Not Cybergeddon, It's Just Tuesday
Using historical examples of cyberattacks, this post stresses the urgency for organizations to reassess their cyber defenses and adopt new technologies to counter evolving threats, arguing that action is critical to avoid predictable disasters.
November 2, 2011: Kaspersky and Cyber Terrorism
This post analyzes Eugene Kaspersky's controversial statements about "cyberterrorism," examining the potential for devastating cyberattacks on critical infrastructure and arguing for a nuanced understanding of cyber threats beyond traditional warfare definitions.
December 28, 2011: Fallout from the Christmas Hack of Stratfor
Using the Anonymous hack of Stratfor as a case study, this post provides practical advice for individuals and website owners to improve their password practices, database security, and overall cyber hygiene.
2012
February 15, 2012: Staggering Your Fiscal Year Is Smart Business
This post analyzes Palo Alto Networks' decision to stagger its fiscal year, arguing that it is a strategic move to mitigate the impact of end-of-quarter sales spikes and ensure consistent financial performance.
March 19, 2012: Mapping the Internet to Wage Cyberwar
This post discusses DARPA's Plan X, a project focused on mapping the internet and developing offensive cyber capabilities, and analyzes its potential impact on the IT security industry, raising concerns about the escalating cyber arms race.
April 2, 2012: Patch Management Best Practices
This post provides a concise guide to patch management best practices, emphasizing automation, vulnerability assessment, and timely patching to mitigate security risks.
May 16, 2012: The Internet is Not Ready for Cyberwar
This post examines a leaked document outlining a planned cyberattack on Iran's electrical grid, expressing concerns about the potential collateral damage and unintended consequences of such an attack.
June 26, 2012: Security Intelligence is the New Black
This post highlights the growing importance of security intelligence in combating targeted attacks, discussing the emergence of dedicated malware research teams within organizations and the need to analyze adversary tactics and techniques.
October 1, 2012: President Obama, Please Veto PPD-21!
This post urges President Obama to veto Presidential Policy Directive 21 (PPD-21), criticizing its provision to map critical infrastructure using satellite imagery, arguing that it would create a centralized target for cyberattacks.
November 26, 2012: Trust is Dead
This post discusses the erosion of trust in digital systems, citing the Diginotar breach and subsequent man-in-the-browser attacks, and highlights the vulnerability of systems reliant on digital certificates.
December 10, 2012: How Big Data is Transforming IT Security
This post explores the transformative impact of big data on the IT security industry, emphasizing the importance of large-scale data collection and analysis for identifying and mitigating threats.
2013
June 7, 2013: NSA Surveillance Threatens US Competitiveness
This post argues that NSA surveillance practices revealed by Edward Snowden threaten the global competitiveness of US tech companies, citing international distrust and the potential loss of business for American firms.
June 14, 2013: Crisis of Confidence Could Spur Flight from US Tech
This post expands on the previous post's concerns, arguing that NSA surveillance has created a crisis of confidence in US technology, potentially leading to a decline in American tech dominance as international customers seek alternatives.
July 29, 2013: Have You Broken Your Confidentiality Agreements?
This post examines the implications of NSA surveillance on confidentiality agreements, questioning whether individuals and companies can guarantee the privacy of their communications in light of widespread government data collection.
August 14, 2013: NSA Surveillance Extends the Threat Hierarchy
This post revisits the Threat Hierarchy model, arguing that NSA surveillance represents a new apex threat, surpassing even nation-state attacks, and predicting significant growth in the IT security industry as organizations seek to counter surveillance.
September 10, 2013: NSA Set to Approve TPM for Government Use
This post discusses the NSA's approval of Trusted Platform Modules (TPMs) for government use, highlighting the potential for both enhanced security and government backdoors, and raising concerns about the future of hardware-based security.
October 28, 2013: How Huawei is Forcing US Tech Companies to Come Clean
This post examines Huawei's statement denying cooperation with government surveillance programs, arguing that it sets a high bar for US tech companies facing accusations of NSA collusion and highlighting the growing distrust in American technology.
November 16, 2013: Trusted Computing Must Repudiate the NSA (updated)
This post calls on the Trusted Computing Group (TCG) to publicly repudiate NSA involvement, arguing that trust in hardware-based security has been irreparably damaged by NSA surveillance practices and calling for transparency and a commitment to user privacy.
December 12, 2013: It’s the Economy, Stupid…and Cyber Attacks
This post argues that focusing solely on national security interests in cybersecurity ignores the reality of a globalized world, urging a shift towards international cooperation and addressing shared cyber threats beyond national boundaries.
2014
January 21, 2014: Ukraine, Cyberwar, and a New World Order
This post analyzes the situation in Ukraine, drawing parallels to previous Russian interventions in Georgia and Estonia, and expressing concerns about the potential for cyberwarfare as a tool of geopolitical manipulation.
February 10, 2014: Wisconsin Needs More Welders, Not PhDs (updated)
This post advocates for a renewed focus on vocational and technical education, arguing that a skilled workforce is essential for economic growth and that a four-year college degree should not be the only path to a successful career.
February 20, 2014: Why Endpoint Security Vendors Fail at Network Security
This post examines the challenges faced by endpoint security vendors attempting to enter the network security market, analyzing the failures of Symantec and McAfee and highlighting the unique demands of network security solutions.
March 18, 2014: How Network Gear Vendors Can Regain Our Trust
This post outlines steps that network gear vendors can take to rebuild trust following revelations of NSA backdoors, including conducting internal security audits, adopting more secure architectures, and communicating transparently with customers.
March 27, 2014: NSA Backdoors in Cisco, Juniper Firewalls Confirmed! Now What?
This post discusses the confirmation of NSA backdoors in Cisco and Juniper firewalls, highlighting the urgency for organizations to take action, recommending specific security measures to mitigate the risks posed by compromised network devices.
May 20, 2014: Sandbox Vendors Ignore Microsoft License Agreements
This post exposes the licensing issues surrounding the use of Microsoft Windows in virtualized sandbox environments, highlighting the potential legal risks for security vendors and discussing how Fortinet and Check Point addressed these challenges.
June 17, 2014: NSA Implant Catalog Confirms Router, Firewall Backdoors
This post analyzes leaked NSA documents confirming the existence of backdoors in networking equipment, discussing the implications for organizations and providing practical advice for identifying and mitigating potential compromises.
August 20, 2014: A Second NSA Leak Spells Big Trouble for the Surveillance State
This post discusses a second major NSA leak, arguing that it further undermines trust in government surveillance programs and will likely lead to increased scrutiny and pushback from privacy advocates and the tech industry.
August 20, 2014: How Pivots Are Creating the New Crop of Fast Growing IT Security Vendors
This post examines the changing landscape of the IT security industry, arguing that strategic pivots and adaptability are key to success for emerging security vendors, and analyzes how companies are adapting to the evolving threat landscape.
September 25, 2014: Shellshock Bug in Bash Could Spawn Worm
This post discusses the Shellshock vulnerability in the Bash shell program, highlighting its potential for rapid worm propagation and emphasizing the urgent need for patching and mitigation measures to prevent widespread exploitation.
October 17, 2014: Cybersecurity Debt Will Bankrupt the US Government
This post introduces the concept of "cybersecurity debt," arguing that chronic underinvestment in cybersecurity is creating a significant liability for organizations, particularly the US government, and calling for increased spending to address vulnerabilities.
November 12, 2014: Thirty-Day Cybersecurity Sprint for the Feds: An Epic Fail
This post criticizes the US government's 30-day cybersecurity sprint, arguing that it is insufficient to address systemic cybersecurity issues and calling for a more comprehensive and sustained approach to government cybersecurity.
2015
January 14, 2015: How the US Navy Hacked the System to Create Network-Centric Warfare
This post details the US Navy's innovative approach to implementing Network-Centric Warfare (NCW) in the 1990s, highlighting their reliance on commercial off-the-shelf technology, overcoming bureaucratic hurdles, and the importance of adaptability in military modernization.
July 27, 2015: What Would a Cyber Pearl Harbor Look Like?
This post encourages readers to engage in thought experiments about potential cyberattacks, arguing that envisioning worst-case scenarios can help organizations identify vulnerabilities, improve preparedness, and strengthen their security posture.
September 23, 2015: How Detroit Taught Me to Hack (and Build) Systems
This post reflects on the author's experience as an automotive engineer in Detroit, drawing parallels between engineering principles and cybersecurity, emphasizing the importance of prototyping, resourcefulness, and a deep understanding of systems.
2017
December 6, 2017: How 5G Is Going to Create a Secure Internet in 5 Stages
This post predicts that the rollout of 5G technology will lead to a more secure internet in five distinct stages, analyzing the impact of infrastructure changes on cybersecurity and highlighting the potential for improved security through network segmentation and encryption.
2019
November 2, 2019: Sandworm Book Review
This post reviews Andy Greenberg's book "Sandworm," praising its chilling account of the Russian GRU's cyberwarfare capabilities and highlighting the devastating impact of their attacks, including the NotPetya malware.
November 7, 2019: Why Palo Alto Networks Will Not Be the Cisco of Network Security
This post argues that Palo Alto Networks, despite its success, will not replicate Cisco's dominance in the network security market, citing the challenges posed by the shift to cloud computing and the evolving nature of network security threats.
December 16, 2019: How Lockheed Martin Invented the Cyber Kill Chain (and MDR)
This post explores Lockheed Martin's pioneering work in developing the Cyber Kill Chain framework and its role in shaping the Managed Detection and Response (MDR) market, highlighting the importance of proactive threat detection and response.
December 20, 2019: It Started with a Spreadsheet: A Short History of Endpoint Security
This post provides a historical overview of the endpoint security industry, tracing its origins from early antivirus solutions to the complex and sophisticated products available today, and analyzing the evolution of threats and the industry's response.
Amazing, right? Here is the DeepDive Podcast, as promised. Enjoy.